Risk management and IT are inextricably intertwined. Organizations are now more aware than ever of the importance of data protection. Consider that, according to Gartner, spends on risk management and information technology solutions globally grew by 12.4% in 2021. Worldwide enterprises are putting more effort is going into discovering, classifying, and assessing sensitive data and personally identifiable information (PII) in order to gain an updated inventory, either in the cloud or on-premises.
Industry experts estimate that by 2024, more than 80% or organizations across the world will need data protection. Which means organizations need to start now to set up regulatory programs, manage large volumes of data, its complexity and numbers of people accessing it, not to mention manage evolving regulations.
Investment in modern data protection strategies is not longer a luxury. But before investing in these strategies, it is imperative also to evaluate existing capabilities, identify potential areas for improvement to drive value, and planning compliance.
The Need for Data Protection
Burgeoning cloud adoption across industry sectors has led to ever increasing volumes and diversity of data being generated. Handling this data and keeping it safe in the face of cyberattacks is daunting. Increasingly we see sophisticated cyber attacks that lead of largescale breaches and compromised data security, which is often fatal of businesses. But, while it is tempting to dismiss cyber attacks as a threat to large organizations, the numbers tell a different tale: 50% of data breaches overall are suffered by small and medium-sized enterprises. Leniency against security risks is the soft underbelly of most organizations; it leaves infrastructure vulnerable to downtime, data loss and financial losses, not to mention regulatory penalties.
What Should Organizations Do?
It is critical to create resilient data protection policies that communicate expectations clearly and set out remediation actions should the threats occur
Organizations need to educate and train not just their their IT security but entire staff about cybersecurity, phishing, and password protection best practices
Other measures include:
Backing up data so as to avoid data loss in the event of any issue, be it a breach, natural disaster or system failure
Data encryption is another line of defence that contains damage from breaches
Reporting and monitoring tools should be leveraged to ensure that implemented data security policies are effective
In the light of growing cloud adoption, it is only natural that the cloud should be the first preference for data protection. And it will only increase, as organizations globally move their back up preferences from on-premises solutions to cloud backup services. But cloud solutions cannot—or rather, should not—be implemented off the shelf; they need to be adapted to suit requirements if they are to provide an effective cloud data protection strategy.
Key Best Practices for Data Protection In The Cloud:
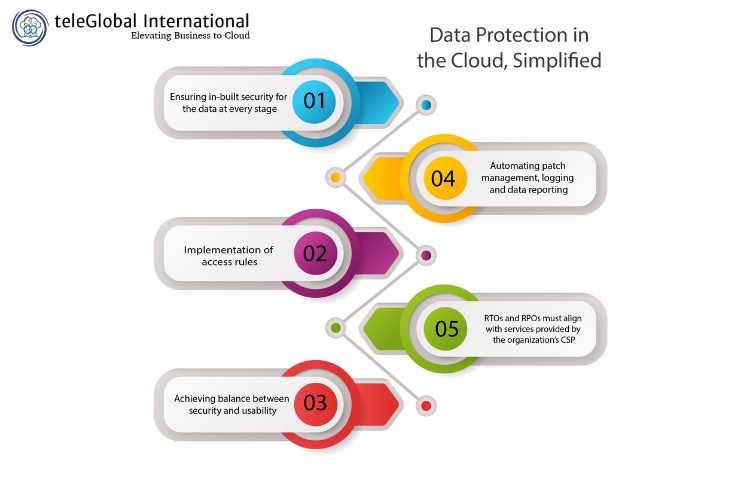
- Ensuring in-built security for the data at every stage, including encryption before the data is saved in the cloud
- Implementation of access rules, including multi-factor authentication (MFA), centralized monitoring, and a governance tool
- Achieving balance between security and usability, viz. optimizing proximity between data protection engines and the user
- Automating patch management, logging, and data reporting, for hassle free audits and to facilitate configuration of security updates
- RTOs and RPOs must align with services provided by the organization’s CSP; this means data must be replicated and stored in secondary storage ready for quick recovery should a disaster occur
- Data Analytics Pipeline: Given that any value that data offers depends on the processing capabilities of organizations, it is essential to adopt appropriate protection methods right from the process of gathering unstructured data, through its refinement, to derive maximum value.
- Data Security Mesh – Individual protection of disparate elements of cloud infrastructure, data, network storage, and application to create a security mesh. This assures location-agnostic data protection.
- Understand the shared responsibility model. It is common to subscribe to the notion that the CSP will take care of data security. This is a common but major error. Most CSPs follow the shared responsibility model, i.e. they are responsible for certain security areas while the organization is responsible for others. A clear understanding of each stakeholder’s responsibilities from the very beginning of the vendor engagement is important for seamless data protection.
- Privacy vs. Security – Encrypted data is private but that doesn’t mean it is secure. So it is important to ensure that authorized users can access the data while guarding against cyber theft. The optimum mix of data privacy and security, depending on the organization’s needs and regulations governing them is key to securing the cloud infrastructure.
- DataSecOps – An understanding that security is an integral part of data operations and not an afterthought prevents potential problems and eliminates the need to for damage control later. This means, the data scientists and IT teams must together build the cloud infrastructure, with data protection as an integral part, effectively melding security and privacy into the cloud.