Managing people, processes and technology is at the core of cloud security, and in order to manage your cloud security, organizations need to put in place policies to protect data and applications in the cloud. AWS gives organizations the control they need to do this. While AWS’s network of data centers and network services are designed and stringently managed in line with compliance needs to protect the cloud itself, the onus to secure applications, identity, access, operating systems, etc., is on the organizations itself. In other words, AWS takes the responsibility to maintain security of the cloud itself, but within in the cloud, the responsibility belongs to the client.
AWS describes this ‘shared responsibility model’. By providing the necessary security and compliances, AWS protects your information assets and workloads. By enabling customers to automate manual security tasks, AWS frees them to focus their efforts on core business matters.
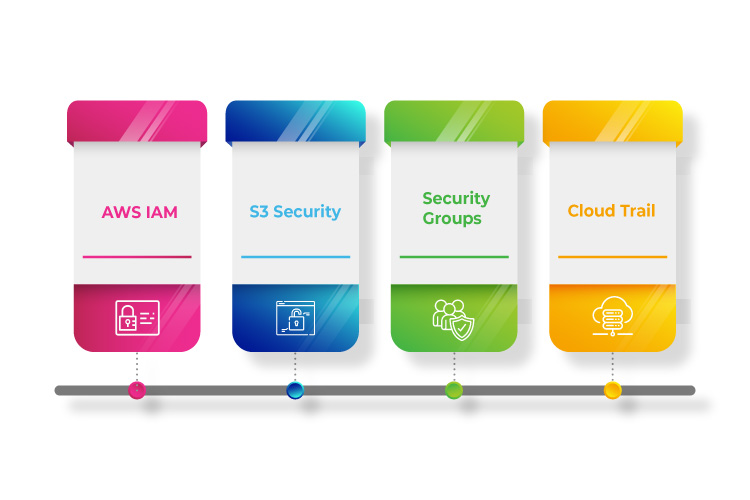
AWS IAM
AWS’s Identity and Access Management enables granular management of which services and resources a user is allowed to access. This micromanagement can be further fine-grained while setting up multi-factor authentication for high-level users, refining control rules, etc.
Best Practices
Some common best practices include:
– Creation of individual users
– Managing permissions for groups
– Grant privileges
– Audit—using AWS Cloud Trail
– Set up password policies
– Allow Multi-Factor Authentication (MFA) for your AWS account, and individual IAM users for that account
– Use IAM roles to secure Amazon EC2 instances, share access, and rotate security credentials.
– Set up conditions to restrict privileged access
– Reduce of remove use of root
S3 Security
AWS Simple Storage Security (aka S3) offers data storage with features to ensure high availability, scalability and performance levels. While, user-access is restricted to the S3 resources they create, AWS enables customers to manage permissions as follows:
IAM: create users and manage their usage access permissions
ACL (Access Control Lists): Allow access to individual objects for authorized users. This is a big benefit for businesses that need to allow access (to files, for instance) to other organizations.
Bucket Policies: Bucket permissions for all objects in a single S3 bucket—a big advantage for organizations that have a mix of public and private files
Query String Authentication: Temporary URLs with a limited-time validity
Audit Logs: For total visibility into access history.
By allowing fine-tuned access control as per your unique business needs or compliance requirements, S3 lets you control costs in line with current needs. S3 works with Lambda, making it convenient for activities like defining alerts and managing workflows without the need to manage additional infra. Thus, Customers of every size and industry can use it to safeguard their data.
Security Groups
Security Groups are a powerful security feature of AWS cloud. Unlike, traditional firewalls which are quite inflexible, AWS Security Groups allow you to specify rules/permissions for both incoming and outbound traffic. The default settings automatically deny traffic unless they are explicitly granted permission.
Cloud Trail
Cloud Trail is a tracking tool to monitor activity. It can tell you how strong your security configuration is, and gives you insights about governance and compliances. Cloud Trail allows you to monitor your infrastructure and usage, track access and activity. These features not only help streamline operations, but bring transparency and accountability into the process, helping organizations boost productivity and avoid or eliminate potential for disputes.
Integrating security into your cloud environment is an imperative, not merely from a regulatory/compliance perspective, but from an operational/efficiency one too. As a matured and independent cloud services provider, Teleglobal helps organizations across industry sectors build resilience into their clouds. Contact our experts today to learn how we can help you secure your IT artefacts in the cloud and optimize your digital investments in the cloud.